That’s right Cloud AD as a services. A fully managed domain by Microsoft : Azure AD Domain Services to manage Azure IaaS workloads.
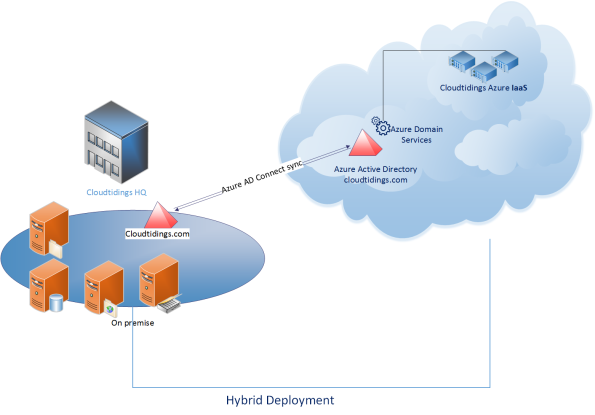
Azure AD Domain Services It’s a cloud based service which gives you a fully Windows Server Active Directory compatible set of API’s and protocols, delivered as a managed Azure service.
You don’t need to provision a Virtual Machine running Domain Controller on Azure as a IaaS anymore and have those domain controllers synchronize to their on-premises Active Directory servers using a VPN/Expressroute connection.
You can now turn on support for all the critical directory capabilities your application and server VM’s need, including Kerberos, NTLM, GROUP POLICY and LDAP.
For scenarios like Disaster Recovery and hybrid cloud deployments, it is just perfect. It means a full value of Windows Server AD in the cloud domain, without having to deploy, manage, monitor and patch domain controllers.
There are many scenarios that can be explored with this new feature.
You can enable Azure AD Domain Services for any existing Azure AD tenant – the same tenant you use with Office 365 or other SaaS applications. Azure AD Domain Services are available now.
For pricing, please check : http://azure.microsoft.com/pricing/details/active-directory-ds/
To start:
- You already deployed Azure AD Connect (to sync identity information from the on-premises Active Directory to your Azure AD tenant. This includes user accounts, their credential hashes for authentication (password sync) and group memberships)
- Create the ‘AAD DC Administrators’ group and then add all users who need to be administrators on the managed domain to it. These administrators will be able to join machines to the domain and to configure group policy for the domain.
- Configure the Network. Select or create the Azure virtual network you’d like to make domain services available in. Ensure the following:
- The virtual network belongs to a region supported by Azure AD Domain Services. See the region page for details.
- Ensure the virtual network is a regional virtual network and doesn’t use the legacy affinity groups mechanism.
- Ensure your workloads deployed in Azure Infrastructure services are connected to this virtual network
![101415_1620_AzureADDoma8]()
- Enable Azure AD Domain Services for your Azure AD tenant, by going to the Configure tab of your Directory, selecting Yes on ‘Enable Domain Services for This Domain’, specifying the domain name and selecting the Azure Virtual Network. Click on Save to confirm.
- Update DNS settings for the Azure virtual network to point to the new IP address of the Azure AD Domain Services you just enabled.
- Enable synchronization of legacy credential hashes to Azure AD Domain Services. This is a required step. By default, Azure AD does not store the credential hashes required for NTLM/Kerberos authentication. You need to populate these credential hashes in Azure AD so users can use them to authenticate against the domain.
A few salient aspects of the managed domain that is provisioned by Azure AD Domain Services are as follows:
- This is a stand-alone managed domain. It is NOT an extension of your on-premises domain.
- You won’t need to manage, patch or monitor this this managed domain.
- There is no need to manage AD replication to this domain. User accounts, group memberships and credentials from your on-premises directory are already synchronized to Azure AD via Azure AD Connect.
- Since the domain is managed by Azure AD Domain Services, there is no Domain Administrator or Enterprise Administrator privileges on this domain.
Tagged: Azure, azuread, Cloud, Identity, Microsoft, PaaS